We reviewed the data on malware blocking among school boards using the D-Zone DNS Firewall and determined that over the three week testing period the DNS Firewall blocked, on average over 50 attempts per school board. Each of these had the potential to cause outages or damage to individual or board IT resources.
Kids these days are so much smarter than the generations before. In fact it has been documented that over the past 100 years IQs have been on a steady climb. Is it nutrition? Global prosperity? The school system? Let’s give credit to all three because it is in light of this fact that we are here to answer the question on the mind of every IT administrator at a school board, university, or collage who has ever had to fix a system corrupted with malware.
If kids are so smart then why do they do so many dumb things (with technology)?
(Note: the same is almost certainly true of corporate IT administrators who may wonder the same of their adult peers).
Schools, more than ever are targets for hackers. They are also harder to secure because they are inherently open environments with student users that cannot be fired for misusing corporate IT resources. Moreover, schools have a user-type that may be more interested than those in other organizations in taking steps to circumvent security without fully considering the consequences. And finally, in the K-12 sector there is a need to implement and appropriately manage filters over inappropriate web content.
This mandate was not imagined when Commodore 64s and 1,200 baud modems were the computer tools of choice. With this in mind we took a look at some of the malware data that we tracked from schools using our DNS firewall.
A snapshot of malware and phishing attempts in a single morning at a single board
In the following table we see a report for a morning’s worth of malware blocking with one of our schoolboard firewall users. In it you can see URLs that look perfectly legitimate to a user that is either unaware of phishing or simply in too much of a rush to be careful. One uses antivirus-googl.com to disguise itself as something good from a trusted entity but with a dash. Another includes the name playstation at the third level of the domain. The last example we will talk about is an impressively targeted phishing attempt using an domain name that used the number “0” instead of the letter “o” and it included both the user name and the name school board (obfuscated out for privacy); 0nlinestore.com/inv/usersnameandschool/78919
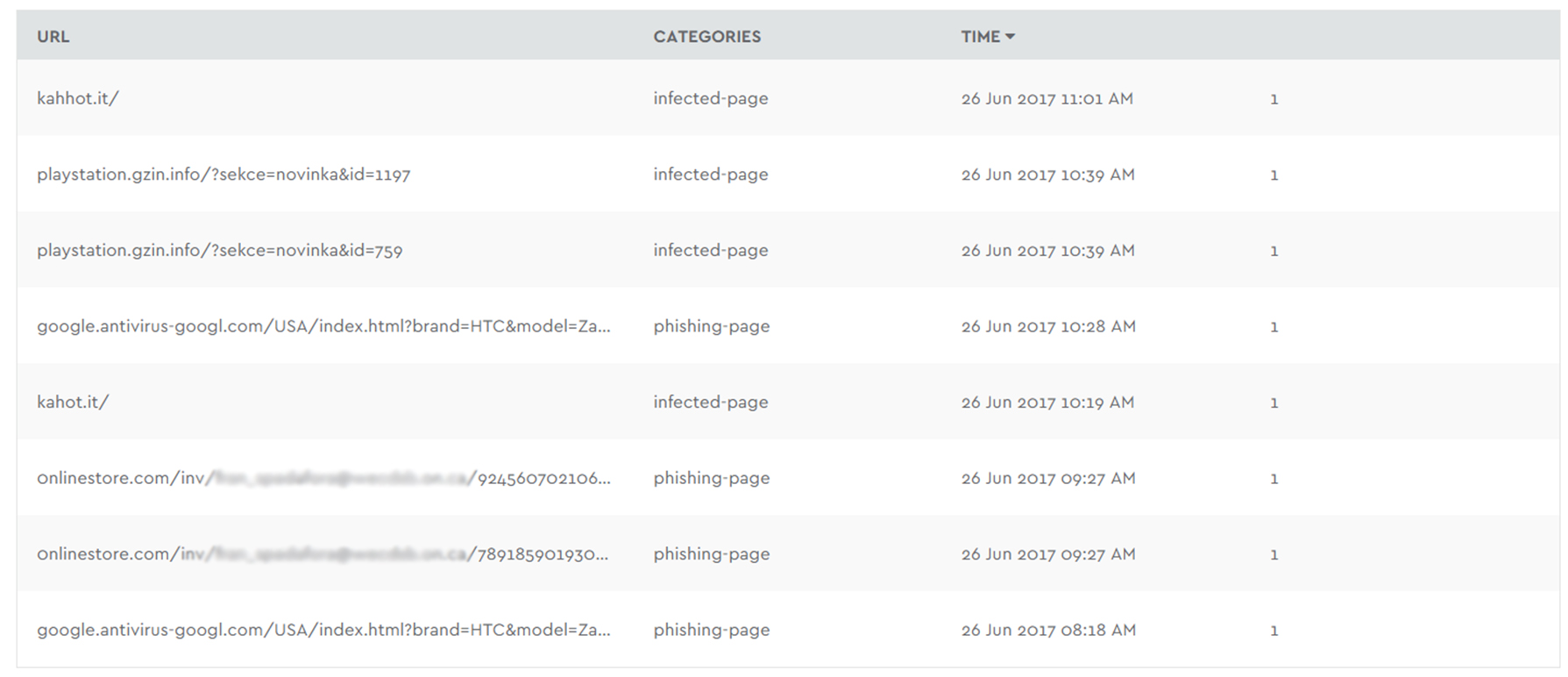
Screen capture showing malware blocks report in D-Zone DNS Firewall
How a DNS Firewall works
CIRA recently launched an education program for our cloud firewall service called, the D-Zone DNS Firewall specifically to help schools address some of their malware/ransomware challenges. It recognizes the special conditions and end-user scenarios that face school boards, colleges and universities face and helps to deliver on one of our non-profit mandates: to build a better online Canada. A bit of technology background is needed before we get into the details. Many are familiar with a traditional firewall as a technology that lives on the edge of your network to keep out bad things. As a DNS firewall it is a similar principal, but it works beyond the network, beyond any firewall, application-layer, or anti-virus protection to add another safety layer that leverages the fabric of the Internet. Our analysis has shown that it catches malware that is often not caught by the firewall to provide an important new layer of defence for those not using one.
When a computer attempts to access a web site it has to reach out to what is called a recursive server on the Internet that translates the website URL typed into an address bar into the IP address computers can understand. This allows the browser to find the computer with the website or online application. We have policy-enabled these recursive servers to refuse answers to visit websites known to contain ransomware and other types of malware. And this malware feed is updated in near real-time against the latest threats. Additionally, because these servers cache multiple requests and because they live in Canadian Internet Exchange points, they deliver a faster end-user experience than other options for recursive servers. In addition to malware, IT administrators can use content filtering to block access to inappropriate content, social media, anonymizers and more. A full set of reports provide information on attempts to access both blocked categories and malware whether from a user click or from when malware already in your network attempts to communicate with its host “command and control” server.
We have aggregated the results of some schools to see just what was being caught in the categories of malware (including ransomware) and content filtering. What constitutes a malware block? Remember that the bad guys are trying to get users to click. The first thing you will notice in these examples is that they could have reasonably come from students, teachers or administration. They also could have come from either clickbait or search. Here are a few examples we catalogued to show they types of links used:
Example 1: Random url type phishing – often a link in an email
7wwtk.2dp.xyz/?v=316G3249FF&kw=952&s2=dffde2c6-e798-4609-9bfc-022816b0643c
Example 2: Traditional legitimate-looking URL used to trick searchers into downloading malware (possible malware site not resolving at time of testing)
comrieknits.com/fathers-day-coloring-pages-for-grandpa/fathers-day-coloring-pages-for-grandpa-1000-images-about-happy-fathers-day-on-pinterest-fathers-day/
Example 3: Anonymizer
Ipconceal.com
Example 4: Adult content
You can use your imagination for this link – we want to keep the blog rated PG-13.
How much malware was prevented during our sample period?
Over the three week testing period the DNS Firewall blocked, on average over 50 attempts per school board to reach sites infected with ransomware or used for phishing. Not every instance is going to result in a catastrophic problem but if even one got through then this defensive perimeter helped to protect both personal and school assets from cost, hassles, and headlines. Since school boards typically want some content filtering, we also blocked hundreds of attempts to reach unauthorized sites that were inappropriate, or even dangerous, in a school environment. In addition to sites that may not be age appropriate we also found that anonymizers represented 27% of blocks and 2% of query attempts to known hacker sites. On the plus side during this timeframe there did not appear to be any attempts to access TOR content.
On the “fun” side we found attempts to reach a tool for building you an essay from pre-existing content (i.e. cheating) and another offering advice on how to fake a sick day. Notably, these attempts reveal a potential dark side of blocking content in overcensoring information either on purpose or by mistake. Therefore, administrators (and parents) need to balance the content needs of the students with their maturity levels and potential browsing risks. In a future blog we will dig deeper into the content policies we are seeing because it can help schools to manage their own policies by understand what their peers are doing.
In conclusion, schools are special environments where controls are inherently difficult to put in place and physical environments are less secure. A defence in depth strategy can help to protect IT resources and a DNS firewall has been shown to be a useful tool in blocking malware.
Interested in learning more about how CIRA is helping education with the DNS Firewall? Visit our DNS Firewall for education page where you can book a meeting for a demo and test account.
Rob brings over 20 years of experience in the technology industry writing, presenting and blogging on subjects as varied as software development tools, silicon reverse engineering, cyber-security and the DNS. An avid product marketer who takes the time to speak to IT professionals with the information and details they need for their jobs.





