Every week, we examine the top trends in malicious activity we have seen in Canada using data obtained through CIRA’s D-Zone DNS Firewall.
One of the advantages of managing a DNS firewall service exclusively for Canadians is that we get a great overview of the cyber threat activity across Canada. This puts us in a unique position as Canada has specific market realities that are often overlooked in aggregated U.S. or North American data.
For instance, a few weeks ago, before bitcoin mining ransomware was making headlines, we saw a spike in bitcoin activity across the network. While that activity has tapered off, it allowed us to get ahead of the issue, inform and protect our customers, and inform other Canadians of the risk.
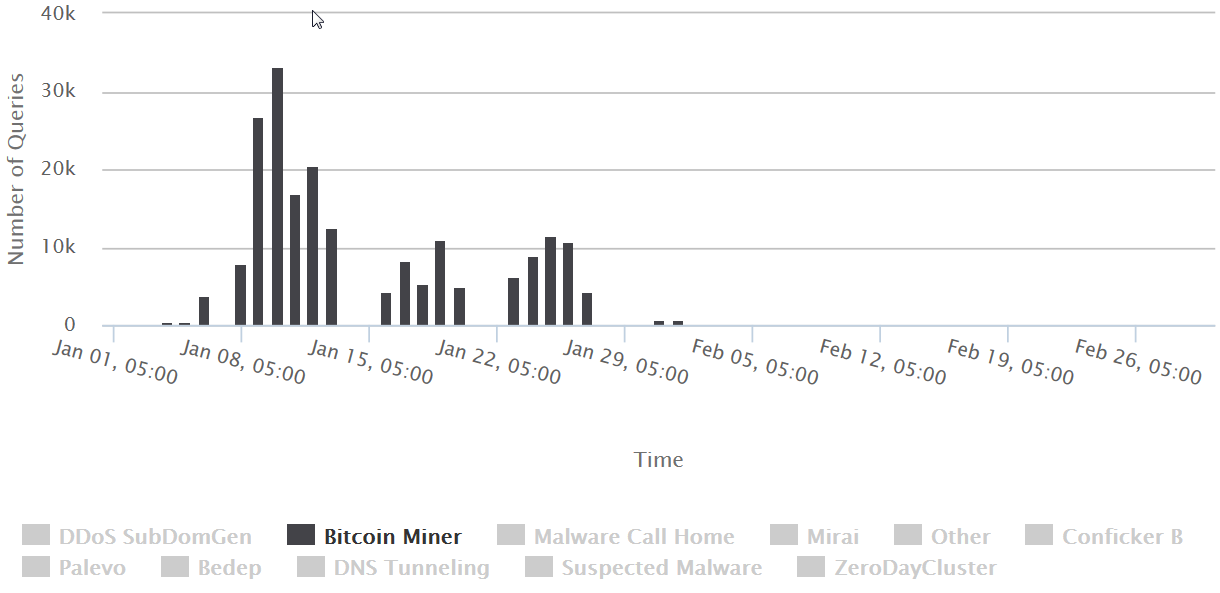
Graph – Historical view of malware traffic specific to Bitcoin miners that spiked back in January and has since tapered off.
Similarly, we see other types of threats come and go that are unique to Canadian organizations. This provides us with data that informs how we build our products and services, and that is reflected in our data science.
As we continue to expand this weekly series on Canadian web security, we are going to expand on these reviews to include more data trends and sector-specific analysis.
In the prior few weeks, we saw some interesting targeted activity using a country-code TLD. This type of activity is unusual as ccTLDs generally have presence requirements that require proof of identification– something the average hacker probably doesn’t want to provide.
Last week, randomized character domains returned to dominance in our top blocks with D-Zone DNS Firewall. These domains are most often associated with malware that generates randomized domains on networks that are already infected.
|
Domain Name |
Category |
|---|---|
|
superyou.zapto.org |
Spybot |
|
dj1.jfrmt.net |
Morto |
|
amnsreiuojy.ru |
VBInject |
|
76236osm1.ru |
Trojan downloaders |
|
ns5.wowrack.com |
Mirai |
|
ns6.wowrack.com |
Mirai |
|
zws12.com |
Malware Call Home |
|
morphed.ru |
Spambot |
|
erwbtkidthetcwerc.com |
Nitol |
|
rterybrstutnrsbberve.com |
Nitol |
Table – Top 10 blocked domains last week and the threat category they belong to.
If you see a random URL, one that seems to be created by an algorithm without much care for human language, it’s a good clue that clicking on it would be a bad idea. Importantly, these queries are often generated from malware that is already on a network as it uses the DNS for execution. Neither scenario is good news for IT administration. The good news is that many algorithms are reverse-engineered so that they can be predictively added to any block lists and stop the threat faster.
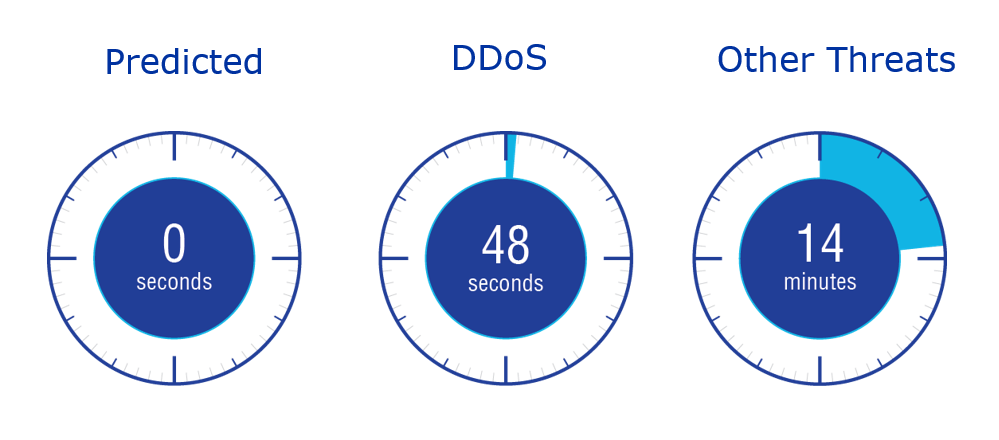
Figure – Speed that we respond to different types of threats showing that predicted domains are automatically blocked.
These randomized domains are not limited to the top 10 blocks. In fact, last week we saw a huge upswing in random domain names versus the rest of March. These spikes indicate an increase in malware activity.
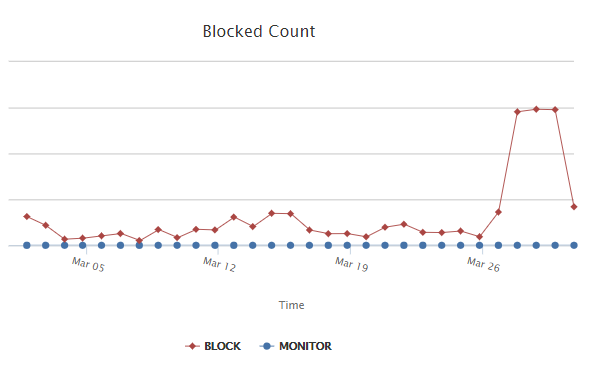
Figure – Number of unique blocked domains has spiked in the last week.
And finally, we are starting to see a modest up-swing in DNS tunneling. This is something that IT managers should be aware of as it can be used to exfiltrate data. With DNS tunneling hackers are able to take advantage of open ports that the DNS needs to pass information and use the DNS protocols (generally the name and UDP message sections) to pass the information. If done correctly the message is encoded so not as easy to spot. We recommend that all IT managers with sensitive data keep an eye out for this.
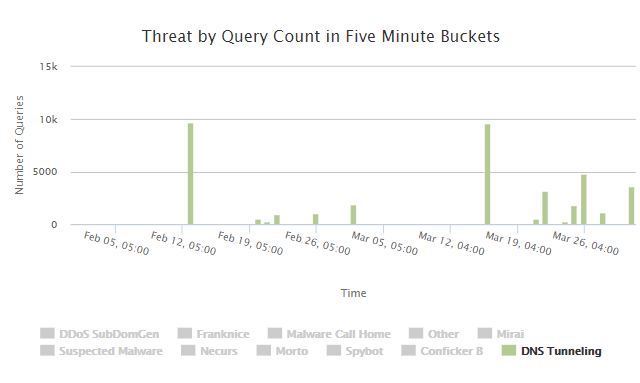
Figure – DNS Tunneling activity over the last two months.
Learn more about D-Zone DNS Firewall.
Rob brings over 20 years of experience in the technology industry writing, presenting and blogging on subjects as varied as software development tools, silicon reverse engineering, cyber-security and the DNS. An avid product marketer who takes the time to speak to IT professionals with the information and details they need for their jobs.





