Every week, we examine the top trends in malicious activity we have seen in Canada using data obtained through CIRA’s D-Zone DNS Firewall.
Many of the top blocked domains this week are indicative of only a handful of infected IP addresses calling out many, many times, while others are more pervasive. Looking at widespread trends can help us analyze cybersecurity trends across Canada – at least among the 800,000 strong user base of D-Zone DNS Firewall.
If we look at the top five threats impacting the largest number of unique IP addresses (or customers) over the last 30 days, one common trend is malware on a network trying to call home. We see this frequently with first-time users of our DNS firewall service who find malware that was already on their network. Another growing trend among hackers is to surreptitiously use corporate networks for bitcoin mining …which I suppose many hackers could consider a “victimless” crime, but I doubt IT managers would feel the same.
Top ten blocked domains last week
|
Domain Name |
Threat Type |
|---|---|
|
superyou.zapto.org |
Spybot |
|
76236osm1.ru |
Trojan downloaders |
|
dzhacker15.no-ip.org |
Hworm |
|
dj1.jfrmt.net |
Morto |
|
api-restlet.com |
Xavier |
|
soplifan.ru |
Trojan downloaders |
|
diplicano.ru |
Trojan downloaders |
|
pumpmywallet.com |
Malware Call Home |
|
ns6.wowrack.com |
Mirai |
|
ns5.wowrack.com |
Mirai |
Definitions of threat types
With all of these different types of threats being shown, we thought it would be helpful to provide a quick description of each.
- Spybot
- A diverse family of worms that allow malicious actions on Windows computers.
- Trojan downloaders
- Botnets that (can) wait for available connections to download malware of various types.
- Hworm
- Microsoft Windows malware that gives an attacker control over the victim’s computer.
- Morto
- A worm that spreads via RDP between Windows machines that have weak passwords – impacts older versions of Windows.
- Xavier
- A Trojan Android ad library that steals and leaks a user’s information silently.
- Malware Call Home
- Domains that are known to be accessed for post-infection communications.
- Mara
- An IoT botnet that is used primarily to launch DDoS attacks. This block also includes variants (e.g. Persirai).
Top four threats in the last 30 days
- Malware Call Home
- Domains used for malware post-infection communications
- Bitcoin Miner
- Any malware whose primary function is using victim computers’ CPUs and electricity to mine bitcoin.
- Malware-Adware/A
- Cluster of malware/adware domains used by hijacked web browsers.
- Suspected Malware
- Suspected malware/botnet activity that is in the process of being classified.
Are things getting better or worse? Lets take a look at the total number of queries over a longer period of time.
Total queries blocked
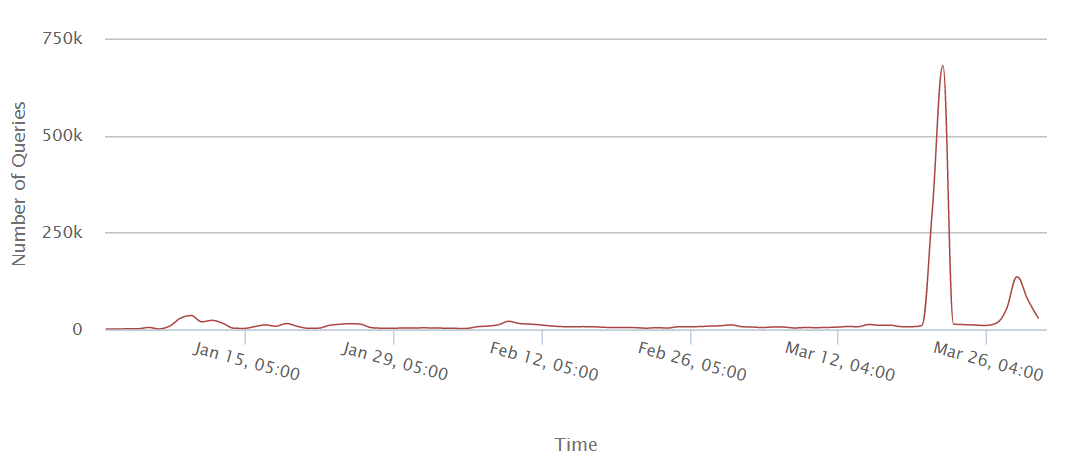
The total number of queries we are blocking – up until the last few weeks, there’s been in a steady-state.
Now to be clear, we aren’t normalizing data and as new customers use our service, the baseline increases but you can see that the last few weeks, malicious query traffic has really stepped up.
Notably, when reviewing the chart, the huge spike was associated with an anonymizer (VPN) that got added to the block list for a very short time before the information was analyzed and rectified. Its prevalence is notable because it illustrates the pervasiveness of VPN technology among users in the educational sector. People using VPNs are often visiting sites associated with risky content and so many corporate users prefer to block anonymizers altogether.
Rob brings over 20 years of experience in the technology industry writing, presenting and blogging on subjects as varied as software development tools, silicon reverse engineering, cyber-security and the DNS. An avid product marketer who takes the time to speak to IT professionals with the information and details they need for their jobs.





