Every week, we examine the top trends in malicious activity we have seen in Canada using data obtained through CIRA’s D-Zone DNS Firewall.
This week, in addition to providing the list of top ten blocks, we’re hoping to help Canadian IT managers understand and manage risk by profiling new threats and interesting security stories.
Earlier this week, the PEI government website was hit with ransomware. While we haven’t seen full details, from what is reported this was likely an automated hack that found a vulnerability to exploit rather than something that found its way in through a user or clickbait. According to Cryptovest, the ransomware demand was a whopping $50US. For that little (as one Reddit poster said, “It costs me $47 to get off the island”), on such an important property, demonstrates that not all hackers are after large sums of money.
The good news is that they were able to restore from backup and carry on their merry way. While this all sounds like a cut-and-dry issue that was solved easily throught the great people and processes in the PEI government, some of the news does underscore the issue when hacks happen. If you read to the end of this CBC article on the subject you get quotes like, “it’s just concerning, they have everybodies information, so doesn’t make you feel very secure.” It illustrates that to IT folks, there certainly seemed to be no risk to data or systems but the public perception can be very different.
So to segue into the planned weekly update, we want to remind everyone how important it is to maintain strong passwords with a few tools that can help.
Tools that can help when an account has been compromised
If you run an IT department, here are a couple of tool recommendations:
1) Gotcha
Cnsider this an important public service announcement from your friendly neighborhood Canadian domain Registry. On this site you can simply enter an email domain address and see what users might have been leaked. The threat is real – on their website, Gotcha states that over 4.2 million Canadian accounts credentials have been leaked.
In addition to data theft, many of these breaches occur through phishing so we’ll also remind you to maintain several strong tools such as spam filters, perimeter firewalls and DNS firewalls to block the latest phishing threats.
2) ‘;–have i been pwned?
For individuals looking for a little more data about themselves, this site can be a real eye-opener because it not only shows the leaks of your account information to the Dark Web, but it also shows more detail on the data breach that made it happen.
For fun you can also type in a password that you have used in the past (probably not recommended to search a current one) and see how often it is has been “pwned”. This can be a good educational tool for your users to stop using “password1”. Find this over at haveibeenpwned.com.
Top ten domains blocked last week
Let’s look at the top domain threats we saw last week from our current D-Zone DNS Firewall user base across Canada. The threat profile has really ticked-up with more nefarious Trojans making up three of the top ten threats and .ru sites continuing to be among the most used. Trojan downloaders can take all kind of nasty turns as they automatically download software that can perform data theft, keylogging and more.
|
Domain Name |
Threat Type |
|---|---|
|
superyou.zapto.org |
Spybot |
|
dj1.jfrmt.net |
Morto |
|
76236osm1.ru |
Trojan downloaders |
|
mastopak.xyz |
Malware Call Home |
|
soplifan.ru |
Trojan downloaders |
|
amnsreiusojy.ru |
VBInject |
|
diplicano.ru |
Trojan downloaders |
|
ns6.wowrack.com |
Mirai |
|
ns5.wowrack.com |
Mirai |
|
buysellstops.com |
Malware Call Home |
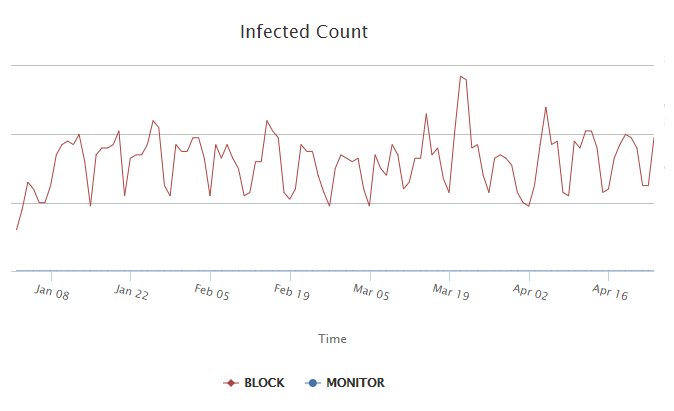
And finally, how are things going overall? For this, let’s take a look back to January of this year at the unique outbound calls (i.e. botnets) per subscriber IP. We see a remarkably static looking trend of quiet weekends and busy weeks. The overall infection count has grown slightly but other than one big spike that was largely the result of a big problem at one large client, the trend on botnet infected clients is one of modest increase.
Rob brings over 20 years of experience in the technology industry writing, presenting and blogging on subjects as varied as software development tools, silicon reverse engineering, cyber-security and the DNS. An avid product marketer who takes the time to speak to IT professionals with the information and details they need for their jobs.





